Introduction
Sign in with Microsoft for WordPress is a Single Sign-on (SSO) authentication flow that provides Entra ID based Single Sign-on for WordPress, for your users to sign into your WordPress website, using their corporate work, school or personal Microsoft account.

Supported features
Open ID Connect based SSO (for Azure AD)
The WPO365 plugin implements the OpenID Connect protocol, which is an identity layer built on top of the OAuth 2.0 protocol […] It provides information about the end user in the form of an ID token that verifies the identity of the user and provides basic profile information about the user […]
Continue reading on the Microsoft website.
SAML 2.0 based SSO (for Azure AD)
Alternatively (to choosing OpenID Connect), administrators can opt to implement the SAML 2.0 based Single Sign-On experience.
Read this article https://docs.microsoft.com/en-us/azure/active-directory/develop/authentication-vs-authorization to understand the differences between OpenID Connect and SAML 2.0.
Single Sign-on (SSO) for Azure AD B2C
Administrators can select whether to enable OpenID Connect (default) Single Sign-on for Azure AD (default) or whether to support Azure AD B2C.
You can find a detailed description how and to what extend the WPO365 plugin supports Azure AD B2C.
Single Sign-on (SSO) with multiple Azure AD tenants
WPO365 can also be configured to support multiple Identity Providers (IdPs). If multiple IdPs have been configured, WPO365 will, by default, render a dropdown list enumerating IdPs by their “friendly name”. A user simply picks an IdP from the list before clicking “Sign in with Microsoft”.
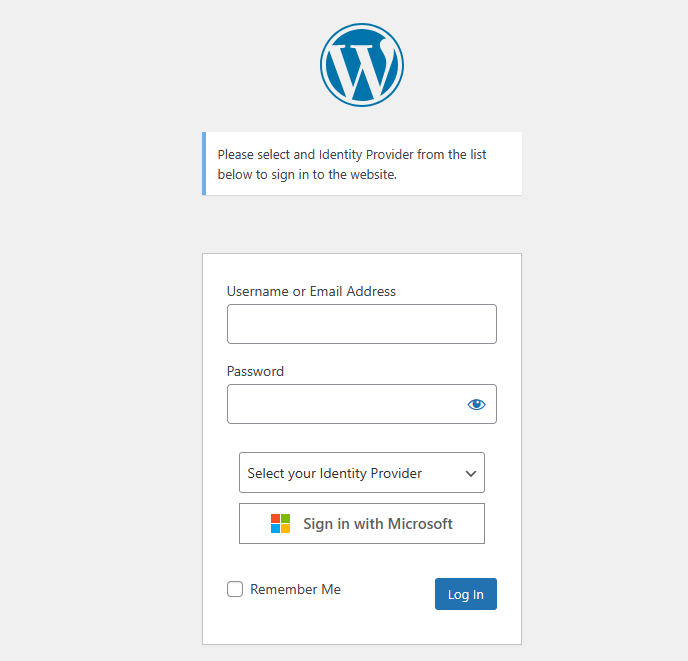
WordPress Intranet / Extranet
Administrators can easily switch between two Authentication scenarios:
Intranet Access to WP Admin and all published pages and posts requires authentication, since a corporation normally would not allow anonymous internet users to read internal corporate information.
Internet Access to WP Admin requires authentication but all published pages and posts are available for anonymous internet users.
Security
Sensitive information, such as a user’s Azure AD / Microsoft Office 365 password is never shared with the WordPress website. Instead, users that sign in with Microsoft do so, in the context of Microsoft’s central authentication portal https://login.microsoftonline.com/. Once Microsoft has established the user’s identity, it provides information about the end user in the form of an ID token. WPO365 will verify the signature of the ID token and also checks the audience (which must match the registered application) and the tenant ID (which must match the configured tenant).
In case of SAML 2.0 the authentication response does not comes in the form of an ID token but instead of a SAML response message. This message has been encrypted using a private certificate which provides an increased level of security. WPO365 verifies the signature of the SAML response and also checks if the message is sent by the configured Azure AD tenant.
Multifactor Authentication MFA
Enterprises that have activate Multifactor Authentication (MFA) or Conditional Access will notice that such policies / restrictions are fully supported by the Open Connect ID and thus by the plugin.
WordPress login
The plugin leaves WordPress’ own login capability intact. Therefore, both WordPress-only users can sign in, when they navigate to the default WordPress login page e.g. /wp-login.php. However, if a user navigates directly to the WordPress admin area e.g. /wp-admin/ then the plugin will send the user immediately to Microsoft to authenticate.
The LOGIN+ extension, allows an administrator to “force” Single Sign-On (SSO) for the (default / custom) WordPress login page. This extension would also allow an administrator to configure support for Dual login. With Dual login enabled, users are not sent to Microsoft immediately, but instead to the default (or custom) login URL.
New user registration
Whenever a user tries to sign into your WordPress website with Microsoft, the plugin receives an ID token. It then tries to find a matching WordPress user by comparing usernames (and if no match is found email addresses). When no matching user can be found, the plugin can create a new WordPress user for you.
The automatic creation of new WordPress users is a configurable option and can be disabled by the administrator.
Please note that the basic WPO365 | LOGIN plugin will not automatically populate a user’s email address, first, last and display name. The WPO365 | PROFILE+ extension takes care of synchronizing a user’s basic profile attributes.
Plugins with these features
(OpenID Connect or SAML 2.0 based) Single Sign-on (for Azure AD as well as for Azure AD B2C) is supported by WPO365 | LOGIN that is available at no cost.
More advanced Single Sign-on features are unlocked by the WPO365 | PROFESSIONAL and the WPO365 | INTEGRATE bundles:
- Support for Azure AD B2C
- Support for Azure AD B2B self-service
- Enable SSO for the login page
- Allow users from other tenants to sign in (Multi Tenancy)
- Require login for selected pages (Private Pages)
- Intercept manual login attempts
- Let users decide how they sign in (Dual Login)
- Single Sign-out for Microsoft 365 services
- Customize the loading template
- Prevent users from changing their email and login
Documentation
- Configure OpenID Connect based Single Sign-on (SSO) for WordPress users
- Configure SAML 2.0 based Single Sign-on (SSO) for WordPress
- Configure Azure AD B2C based Single Sign-on (SSO) for WordPress
- Configure multiple Identity Providers

